Resource savings
Decrease costs, increase program efficiency, and comply with privacy request requirements with a single platform that handles every step — all without human intervention.
Coverage without complexity
No matter the data system, request type, regulation, or requirement, Transcend has you covered, with customization as easy as checking a box.
Reduced risk
Built to be secure by design with single sign-on in every plan, plus self-hosted security gateway with end-to-end encryption and flexible key management.
RESOURCE SAVINGS
Better outcomes with hands-free privacy requests
Cut privacy request processing costs by up to 80% or more and ditch manual work. Get started with Transcend Privacy Requests in minutes, and access prebuilt workflows and zero-code customization to fully automate data requests — no humans required.
COVERAGE WITHOUT COMPLEXITY
Engineered to fit your unique needs
Whatever your industry or scale, data system or compliance regulations — you name it, Transcend handles it all. We've engineered Privacy Requests with flexibility, so you can overcome the privacy hurdles of today and the needs of tomorrow with peace of mind.
await transcend.post('/v1/data-subject-request', { email: 'ben.farrell@example.com', coreIdentifier: userId, type: 'ACCESS', });
Submit a request programmatically to Transcend to be processed. Or, use Transcend's no-code Privacy Center to receive requests.
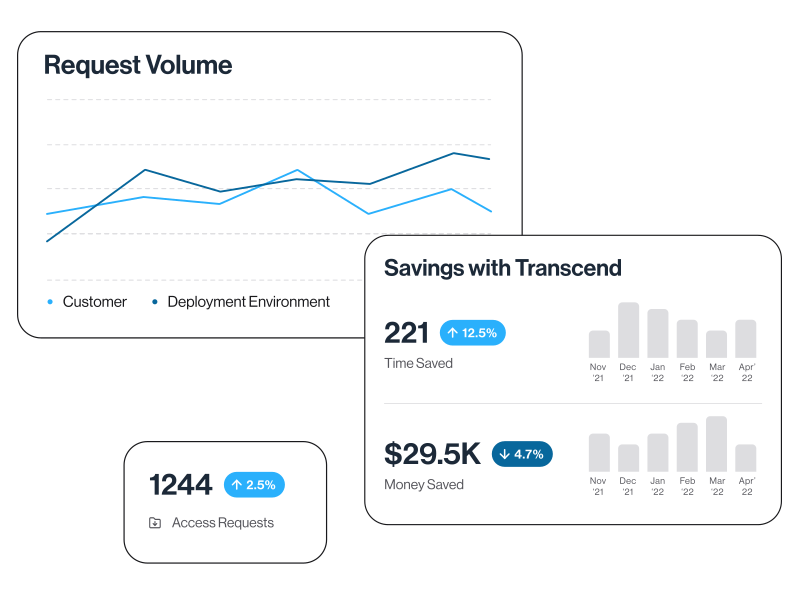
IMPROVED VISIBILITY
Understand your privacy metrics like never before
Ditch manually consolidated report spreadsheets and get a comprehensive view into all your key program metrics. From request trends to cost savings calculations - Transcend gives you the insights you need to fully analyze, visualize, and share your privacy program’s impact.
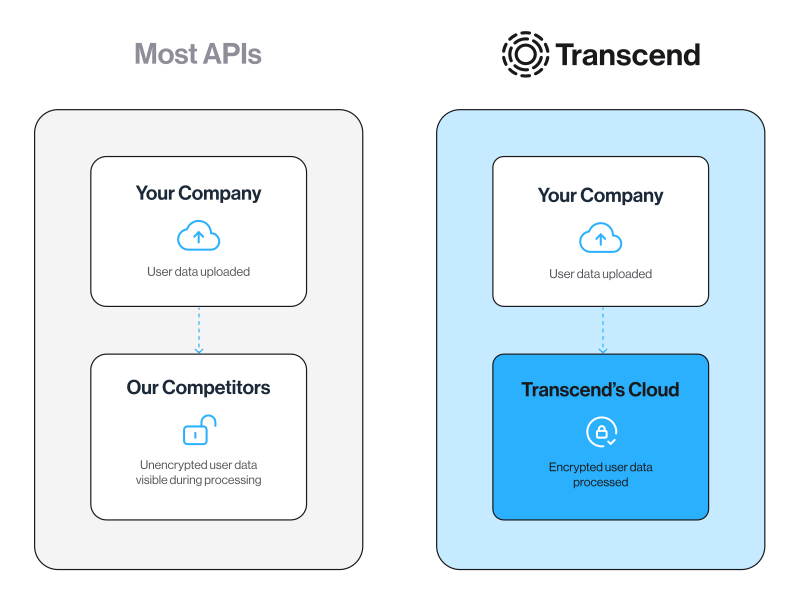
REDUCED RISK
Designed to reduce breach risk, not add to it
Transcend is engineered from the ground up to be secure by design. Using our industry-leading self-hosted security gateway, your data is encrypted within your firewall—meaning we can't access your keys, we can't see your user data, and we can't forge a request to your system. Plus, get granular access controls and single sign-on, included on every plan.
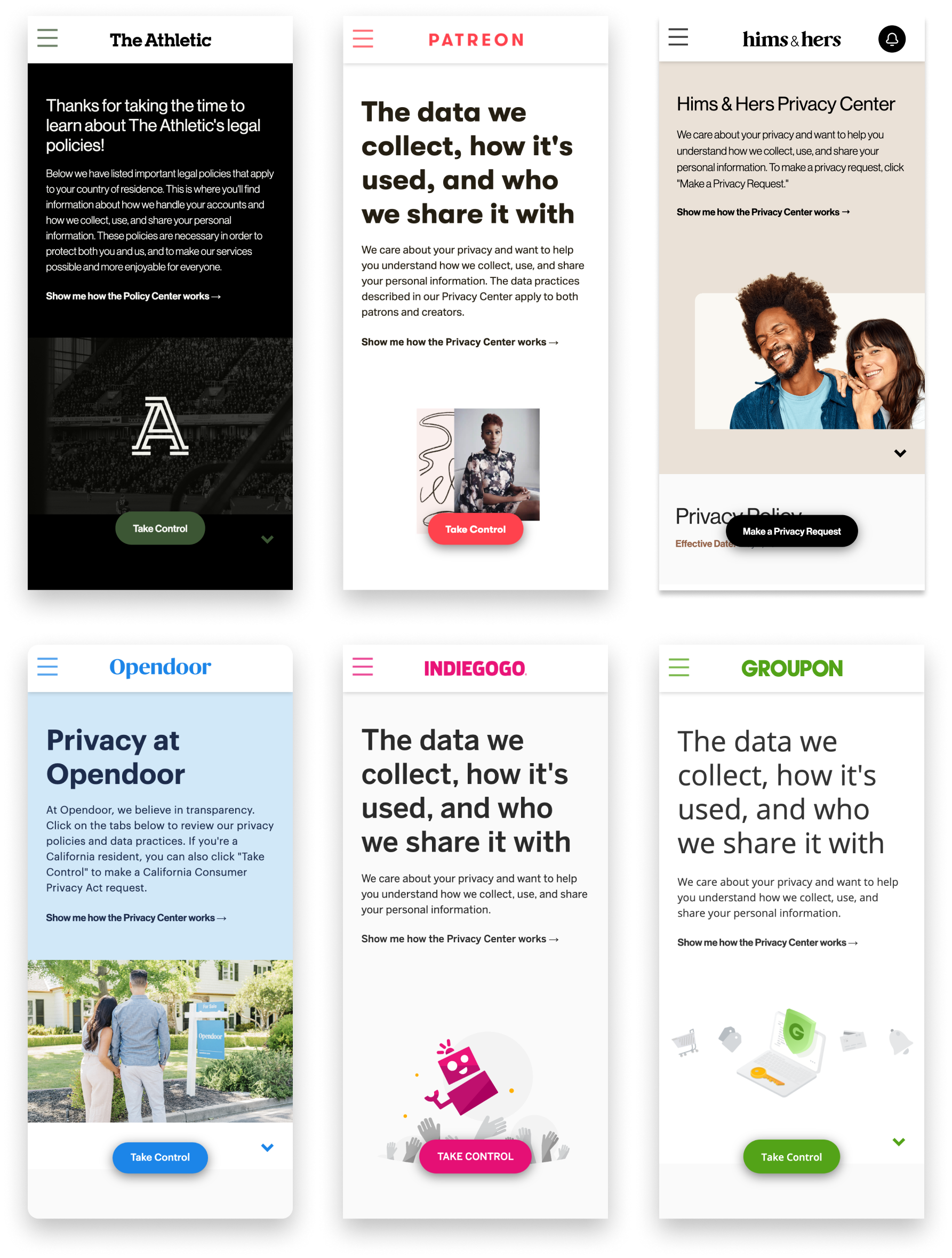
PRIVACY CENTER
A powerful way to give your customers self-serve privacy control
Our self-serve Privacy Center moves you beyond legacy web forms or outdated email inboxes — it gives you an enterprise-level, scalable, secure way to handle privacy requests and subsequent communications. Give your customers direct control over their data, in just a few clicks.

Into the future of privacy
We make it simple for top brands to lead the way on privacy and give their users control of their data.
7M+
Access & erasure requests fulfilled to date
77 hours
Saved per 100 requests
"Not only is Transcend a comprehensive tool that handles user verification and integrates with our many SaaS tools and internal databases, their dev tools allow us to quickly configure access and deletion requests and classify datapoints directly in code, saving us countless hours."
Chris Woods | Software Engineer, Orchard
"When we started looking for a privacy tool, TechGC peers and other legal colleagues all pointed to Transcend as the leader in automated privacy solutions, with top tier support and education. From there, each engineer I brought into our conversations was immediately impressed with Transcend, further validating the power of their technology."
Keara Roethke | Legal Director, Snapdocs
“Our Creators and Patrons may be looking for instructions on account deletion or just checking in on the status, and we use Transcend to quickly look up customers and provide immediate answers to our users. Working in Customer Support, we need answers as soon as we can get them – Transcend helps me do my job well.”
Maria João Medeiros | Customer Support
"During the onboarding process, we asked ourselves a number of questions, including: How streamlined is this solution? Does this fully automate our needs and that of our users? Does this meet and exceed our requirements on security and legal compliance? Is engineering on board with the solution and is it an easy lift for them to integrate? The answer for all of that was a ‘yes’ with Transcend."
Frankie Benjamin | Privacy Program Manager, Indiegogo
"Transcend quickly put our entire DSR process on autopilot–from redacting unstructured data in Slack to implementing identity enrichment using Looker. Our data silos are hit with high volumes of requests every day, and we have a lot of silos. We've saved thousands of hours because of Transcend’s automation and feel confident that we’ll keep up with future regulations with minimal eng maintenance."
Privacy Specialist | Global Consumer Delivery App
“Clubhouse is in high growth mode with a nimble engineering team. We needed a strong data privacy partner that could immediately add value and that could keep up with our expansion, with the right stack to meet our needs as we grow. Transcend has helped us get a handle on several important aspects of privacy engineering so we can solve things the right way for our community.”
Taylor Hughes | Trust and Safety Engineer, Clubhouse
"With Transcend, A Cloud Guru has saved a massive amount of time and resources, removing manual processes and working seamlessly across our SaaS tools and internal databases. Transcend has been instrumental in bringing our privacy program to an automated, security-by-design state."
Benjamin Mullen | Director of Product Security, A Cloud Guru - now part of Pluralsight
.svg.png&w=384&q=75)
"The Transcend platform is built with automation at its core–table stakes for any modern, global company. But it’s the extensibility, flexible developer tooling, and knowledgeable support and engineering teams, that make it easily adaptable to the edge cases, massive user volumes, and tight timelines, every enterprise company is faced with. Transcend makes privacy compliance more manageable… even fun."
Alex Johnatakis | Security and Privacy Engineer, True Search
“We fundamentally shifted our approach to data privacy in April 2019 to be more user-centric, and worked with Transcend to include more transparency on our data practices and offering immediate data access to our millions of users. When we took this approach, we were flooded with hundreds of thank you tickets.”
Priya Sanger | Deputy Legal Counsel, Patreon
“Transcend is a rare example of a vendor who has become a true partner. Our questions are answered so quickly - it feels like we’re on the same team. Transcend’s technology is impressive, but it’s the incredible support that takes it to the next level.”
Piotr Wurst | Data Privacy Specialist, Groupon
Frequently asked questions
- What types of data subjects do Transcend Privacy Requests fulfill requests for?
- Can Transcend Privacy Requests handle employee DSARs under CPRA?
- What types of data actions does Transcend support?
- What data systems does Transcend connect to?
- How does Transcend authenticate the user making a request?
- Can I partially integrate Transcend into my existing operations?
- Can multiple teams interact with the Transcend platform?
- What is the Privacy Center? How do I configure it?
- How is Transcend secure by design?
- Does Transcend maintain audit logs?

